In fact, they're tracking every download and selling the data to the music industry. How one company is turning file-sharing networks into the world's biggest focus group.
By Jeff Howe
Joe Fleischer twists restlessly in his Aeron chair and nods at the voice on the other end of the telephone. Tapping his fingers on his computer's mouse, he stares out the window of his Beverly Hills office at the new BMWs and battered Celicas inching down Wilshire Boulevard. "Uh-huh, uh-huh," he says. "Got it." Fleischer is talking to a client, an executive at one of the major labels who's working a band he's sure could go platinum, if only radio would give the group a chance. The band's first two albums earned it a fervent fan base, but to get bigger, its new single needs airplay, the all-important spark of sales. "Give me a story I can take to radio," the executive on the other end of the line tells him.
Fleischer hangs up, turns to his computer, and clicks through an online database. On his screen, he can see in astonishing detail when, where, and what Internet users are sharing on peer-to-peer file-swapping services like Kazaa, Morpheus, and Grokster. He searches for cities where downloads of the band's single are outpacing its exposure on radio. He likes what he sees. In Atlanta, sharing of the group's new album is up more than 1,200 percent over the previous week; in Houston and New York, 300 percent. So Fleischer checks to see how much airplay the track is getting on alternative rock stations in those markets. Very little, it turns out - less than five spins per week in each city. "Jesus," he whispers. In Houston, "KTBZ only spun it once, and it still got into the top 15 downloads. This is hot."
In the argot of the industry, what Fleischer sees is reactivity: the single most important quality a song can have. Basically, it means listeners can't get that tune out of their heads - they probably downloaded it after hearing it only once - and radio stations ought to put the track in heavy rotation. Usually, programming executives evaluate songs by call-outs, telephone surveys in which people hear a clip and give an impression. But that information isn't very helpful to labels, Fleischer will tell you, because it doesn't apply to album sales.
Fleischer is VP of sales and marketing for a company called BigChampagne, which has a better window into consumer demand. By matching partial IP addresses to zip codes, the firm's software creates a real-time map of music downloading. The company sells subscriptions to its database that let a user track one album for $7,500; bigger labels have annual deals for up to $40,000 per month.
He calls his client and gets voicemail. "Dude, you're gonna be stoked," he says. "I'll shoot you an email in a few minutes." In the office, Fleischer seems 39 going on 18, a Valley Boy with a baby face and a sly grin. He has music in his blood - his father was a studio musician who played with Frank Sinatra and Herb Alpert and the Tijuana Brass, and Fleischer himself is a band manager in his spare time. I ask how the label executive will use the data. "He'll give this to promotions," he tells me. "They'll call these stations and say, 'You need to bang this shit. You're barely playing it, and it's already in the top 15 among alt-rock downloaders in your market. You need to step on this at least 20 more times a week, and not while people are sleeping.'"
A week later I call Fleischer to find out how his client reacted. When the executive showed the data to the label's general manager, Fleischer says, "the GM came around his desk and hugged him."
According to on-the-record statements by many major labels, the scene I witnessed in Fleischer's office couldn't possibly have happened. But Eric Garland, CEO of BigChampagne, says his firm is working with Maverick, Atlantic, Warner Bros., Interscope, DreamWorks, Elektra, and Disney's Hollywood label. The labels are reticent to admit their relationship with BigChampagne for public relations reasons, but there's a legal rationale, too. The record industry's lawsuits against file-sharing companies hang on their assertion that the programs have no use other than to help infringe copyrights. If the labels acknowledge a legitimate use for P2P programs, it would undercut their case as well as their zero-tolerance stance. "We would definitely consider gleaning marketing wisdom from these networks a non-infringing use," says Fred von Lohmann, staff counsel for the Electronic Frontier Foundation, the San Francisco-based cyber liberties group that's helping to defend Morpheus, Grokster, and Kazaa.
But even as the industry as a whole litigates, many of the individual labels are quietly reaching out to BigChampagne, turning file-sharing networks into the world's biggest focus group. In the beleaguered music business, this market research strategy that dare not speak its name is fast becoming the Nielsen ratings of the peer-to-peer world.
You can't blame the music industry for wanting to know more about its consumers. "For years," says Ted Cohen, a senior vice president at EMI, "the mantra of the record biz was, you don't need research. It was, 'This song sounds great, so just play the fucking song.'" Currently, radio relies on call-outs, and the labels rely on SoundScan, a subscription-based service that tracks album sales at the point of purchase and organizes them according to zip code. Neither offers any information on reactivity or what kind of fan is listening to what kind of music.
BigChampagne does. "It's fantastic," says Jeremy Welt, head of new media at Maverick Records, an AOL Time Warner label. "It actually shows us what people are doing of their own accord." And because radio is beginning to take BigChampagne seriously, Welt says, Maverick can use the figures to persuade stations to increase spins.
"The fact is, P2P is a likely distribution channel for our wares," says Jed Simon, head of new media for DreamWorks Records. "If we're going to be intelligent businesspeople, it behooves us to understand it." BigChampagne is happy to provide that understanding, even if it has to operate on the sly.
For most customers, Garland says, "we're the mistress." He and his colleagues once met with some executives from a major label on the street near the label's offices, just to avoid setting off gossip. But not everyone is afraid to be seen with BigChampagne. In March, the company signed a deal with Premiere Radio Networks, the subsidiary of radio giant Clear Channel that sells research products, including the airplay-tracking system Mediabase. The agreement gives the two companies access to each other's data and lets Premiere sell packages of information that include the BigChampagne product.
Radio stations need to measure reactivity even more than labels do, and Garland says the package has exceeded sales targets. Erin Bristol, program director at Clear Channel's Hot 107-9, a Top 40 station in Syracuse, New York, began looking at BigChampagne before the deal. "A lot of radio airplay is based on what other stations are doing, and that's silly," Bristol says, "because what's going on in New York or LA isn't necessarily indicative of what's going on in Syracuse." For example, she might not have added the Kid Rock- Sheryl Crow duet "Picture" to her playlist ("which leans rhythmic") until she noticed that local file-sharers were sucking down the song. "I threw it into my call-outs, and it was reactive, so we made it a subpower," a song that plays 40 to 50 times a week. Bristol says she was turned on to BigChampagne by an executive from Warner Bros. but asked me not to name him.
Have you ever watched file-sharing? I mean really watched file-sharing? I'm in BigChampagne's Atlanta office, where several of the company's dozen or so employees have gathered in the conference room to show off the firm's technology. Garland is filling me in on how he started the company, but I can't take my eyes off the green digits raining down on the big black screen behind him in a matrix of file-sharing. I interrupt him to ask the coders if they can freeze the display. One of them taps a few keys, and the blur atomizes into individual search requests. One user - BigChampagne's software doesn't retrieve actual IP addresses, only a cipher corresponding to metro area - wants to hear the Goo Goo Dolls. Another is interested in "endurance bondage-caning." "A lot of people," COO Adam Toll notes, "are looking for porn."
Garland spent much of his twenties working as a management consultant, dashing through airports and hotel restaurants telling people how to run their businesses. File-sharing was an obsessive hobby; he scoured nascent P2P networks for obscure Britpop. In early 2000, he quit his job and moved to LA. One night when he was out drinking with his friend Glen Phillips, former vocalist for Toad the Wet Sprocket, they began discussing Napster. Toad's heyday had passed, but that hadn't deterred fans from swapping warehouses' worth of the band's music. Phillips, who was trying to jump-start a solo career, "wanted to figure out a way to capitalize on that popularity."
Garland called Zack Allison, a friend from Rice University who was exploring distributed-computing applications. Allison built a program that sent anyone sharing a Toad song an invitation to join Phillips' mailing list, and they decided that if it looked promising they would start a business. "The opt-in rate was 20 percent!" says Zack's father, Tom. "A good opt-in rate is usually 2 or 3 percent." Dapper in a mild fashion, Tom Allison, 60, approaches marketing with a near-religious zeal; he spent 36 years working with Coca-Cola's marketing department, the Los Alamos of consumer research. When Zack called to tell him about their business idea, he realized the real money was in the data and agreed to serve as an incubator and de facto den father for the startup. In a nod to the music industry's dour situation, they took their name from a line in Peter Tosh's apocalyptic "Downpressor Man": "You drink your big champagne and laugh."
In the summer of 2000, Garland and the Allisons hired coders to build software capable of recording and archiving the contents list of shared folders and 50 million search queries a day, and Garland and Tom Allison began pitching their service to labels. At first companies demurred, figuring the courts were about to solve their Napster problem. But then scores of copycats sprang up to replace Napster - the research firm NPD Group estimates that 31 million Americans shared music from a P2P service in September 2002.
Tom Allison and I leave the company's headquarters and drive to a warehouse district on the outskirts of Atlanta. Here, in the dark basement of a brick building, BigChampagne's programmers monitor the software that tracks 50 million search requests a day. "They hate natural light," Garland says of his team, several of whom scowl vaguely at the intrusion.
Although the company's storage needs are substantial, the real heavy lifting, in both bits and man-hours, involves processing the data and presenting it through an easy-to-use interface. Search entries are never uniform ("Rhonda" vs. "Help Me Rhonda") and rarely literate ("Hepl me Rhoda"), and over the past few years the company's coders have fine-tuned a series of programs that clean and organize what they pull off the Internet into a form that can feed the database. BigChampagne's clients can pull up information about popularity and market share (what percentage of file-sharers have a given song). They can also drill down into specific markets - to see, for example, that 38.35 percent of file-sharers in Omaha, Nebraska, have a song from the new 50 Cent album.
What lets the service transcend trivia is the way it establishes correlations between artists. By recording the entire contents of users' shared folders, BigChampagne can determine that, say, 58 percent of people with a Norah Jones song also have at least one track by John Mayer. This lets the company categorize users by radio format, as well as provide solid information about what kind of listener is making a certain single reactive.
To some, though, the accuracy of that information is an open question, and even BigChampagne itself cautions that its service is better at determining trends than exact quantities of downloads. File-sharing is notoriously difficult to monitor, especially since the IP addresses used to track it don't always map to individuals. Jay Samit, former digital media chief of EMI (he recently announced he was leaving to take a position at Sony), says he's skeptical of any reresearch based on IP addresses. "It's like buying gifts on Amazon: Say I get Joy of Cooking for a friend - that suddenly changes my profile." The marketing plan he might employ for an "angry rock rebel" is very different from the one he'd use on a soccer mom, and "just knowing they're both in Tulsa doesn't help me." Because AOL works with dynamic IP addresses, Samit notes, the location of its users can't be determined. (The company says that AOL subscribers account for only 15 percent of its information and that it includes them in its national, but not local, data.)
After spending three years convincing the music industry of the utility of P2P data, BigChampagne now faces challenges from a number of directions. An LA company named Webspins is offering a similar service, and the two firms have since filed lawsuits against each other for defamation and unfair business practices. And in July, Billboard launched a new chart that monitors sales of downloads from legitimate services. Right now, by monitoring peer-to-peer networks, BigChampagne tracks nearly all the music downloaded from the Internet. But that will change as industry-sanctioned music services like Apple's iTunes gain more of a foothold.
In the meantime, BigChampagne is beginning to diversify. In May, Garland started talking to two major Hollywood studios (contractual obligations prohibit saying which). Over the long term, the entertainment industry will never stop worrying and learn to love file-sharing - but BigChampagne will help them learn to live with it.
Contributing editor Jeff Howe (jeffhowe@wiredmag.com) wrote about the music business in Wired 11.02
















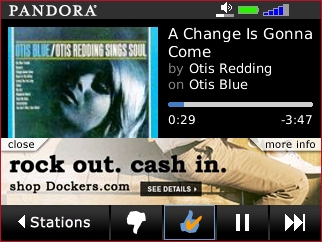 One of those apps is the mobile edition of Pandora, the original programmable radio stream that learns your musical tastes as you listen. Having Pandora in my pocket is reason alone to own a mobile handset; my friend Angela
One of those apps is the mobile edition of Pandora, the original programmable radio stream that learns your musical tastes as you listen. Having Pandora in my pocket is reason alone to own a mobile handset; my friend Angela 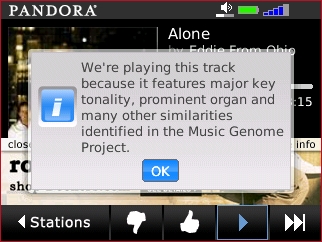 The Mobile Pandora isn't as conversational as the PC edition -- for instance, you can't go into your profile and load up all your bookmarks. You can get an explanation why you're hearing the song you're hearing, and this little feature alone shows you why the System upgrade was necessary -- on the old system, there's no way this information would be the least bit legible in a single alert box.
The Mobile Pandora isn't as conversational as the PC edition -- for instance, you can't go into your profile and load up all your bookmarks. You can get an explanation why you're hearing the song you're hearing, and this little feature alone shows you why the System upgrade was necessary -- on the old system, there's no way this information would be the least bit legible in a single alert box.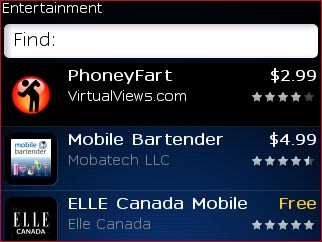 The upgrade process will back up your existing calendar, e-mail, media, and personal applications automatically, and will restore them after the new modules are loaded in and verified. The verification process, for some reason, is the longest stage -- be prepared to wait as long as 45 minutes. The process in its entirety could take an hour, maybe a little longer.
The upgrade process will back up your existing calendar, e-mail, media, and personal applications automatically, and will restore them after the new modules are loaded in and verified. The verification process, for some reason, is the longest stage -- be prepared to wait as long as 45 minutes. The process in its entirety could take an hour, maybe a little longer. You'll notice some differences right away, some thanks to the new system, others on account of smart users who truly appreciate the low value of farting apps. The catalog is much more pleasant to read, even if -- sadly -- some of the entries haven't changed all that much since App World's premiere earlier this month. The "before" and "after" pictures above tell the story. ("ECOE" isn't very self-explanatory, is it? It's a Ticketmaster application, so you'd think it would have been named something like "Ticketmaster Application.")
You'll notice some differences right away, some thanks to the new system, others on account of smart users who truly appreciate the low value of farting apps. The catalog is much more pleasant to read, even if -- sadly -- some of the entries haven't changed all that much since App World's premiere earlier this month. The "before" and "after" pictures above tell the story. ("ECOE" isn't very self-explanatory, is it? It's a Ticketmaster application, so you'd think it would have been named something like "Ticketmaster Application.") This is the history of the most relevant food for human
This is the history of the most relevant food for human




